Javascript Injection – The Saga Continues
If you have been keeping up, I have been posting about ongoing hacks and injections that have hit several of our client websites. Well, we have another to add to the list and hope this information helps you clean up your site as well.
HCIFX.COM (Javascript injected)
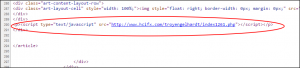
One of my primary business sites was accepted by Google as cleaned and then within a month, rejected again. This time, I found a javascript injection happening throughout the site. The culprit was living in the database. Since it was living in the database, the scans that my host conducted for me, showed the site as “clean”. Very sneaky. Here is the quick way to get rid of this (very common apparently) string of code.
URL BEING INJECTED: http://www.hcifx.com/troyengelhardt/index1261.php
Yes, Troy Engelhardt a designer in Indiana, owner of hcifx.com. Why his domain and name are in my website left by a hacker is unknown to me. Did he do it? I do not know. Was he attacked as well? I do not know. None of that matters right now (although we will be investigating this matter future). What matters right now is getting your site cleaned so that you can get relisted in Google and fast.
Removal Process
Step 1
Visit your cPanel or Hespia CP and access your database. If you have a ton of sites on your account, you can find the name of your database in the wp-config file within your WordPress website.
Step 2
Always back up your website and/or database before you work on them. In this case, back up your database first.
Step 3
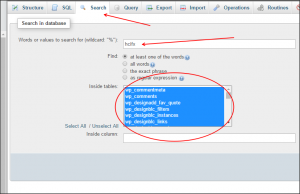
Once your phpmyadmin loads your database, click on your database name in the left frame. All of your tables will load on the right side. Click on “Search” at the top. You will start by searching for hcifx.
You will want to search all tables. Press “go” (bottom right).
Step 4
Once your results appear, if you are like me, you will quickly see where the results are. I had 453 instances. Next to the table it will say “Browse” or “Delete”. I would not recommend deleting this search result. What you will need to do is repeat the search but this time put in the WHOLE string as it appears in your website source code. Once you complete the second search, go ahead and press “Delete” next to the results. NOTE: You may want to “Browse” first to make sure that the results do not include any of your legitimate posts or pages.